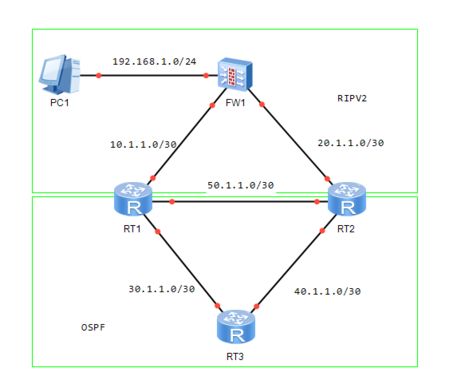
拓扑如图↓
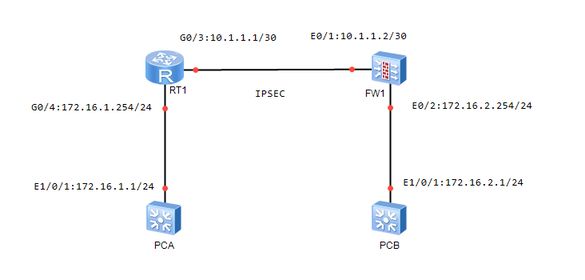
设备型号
FW1:DCFW-1800 Version 4.5
PCA:DCRS-5650 Version 7.0.3.1
PCB:DCRS-5650 Version 7.0.3.1
RT1:DCR-2655 Version 0.4.2
配置IP与路由
DCRS-5650模拟PCA
DCRS-5650-28(R4)(config)#hostname PCA
PCA(config)#vlan 233
PCA(config-vlan233)#int vlan 233
PCA(config-if-vlan233)#ip add 172.16.1.1 255.255.255.0
PCA(config-if-vlan233)#exit
PCA(config)#interface ethernet 1/0/1
PCA(config-if-ethernet1/0/1)#switchport access vlan 233
Set the port Ethernet1/0/1 access vlan 233 successfully
PCA(config-if-ethernet1/0/1)#exit
PCA(config)#ip route 0.0.0.0 0.0.0.0 172.16.1.254
RT1
Router_config#hostname RT1
RT1_config#interface gigaEthernet 0/4
RT1_config_g0/4#ip address 172.16.1.254 255.255.255.0
RT1_config_g0/4#interface gigaEthernet 0/3
RT1_config_g0/3#ip address 10.1.1.1 255.255.255.252
RT1_config_g0/3#exit
RT1_config#ip route 0.0.0.0 0.0.0.0 10.1.1.2
FW1
DCFW-1800(config)# hostname FW1
FW1(config)# interface ethernet0/1
FW1(config-if-eth0/1)# zone untrust
FW1(config-if-eth0/1)# manage http
FW1(config-if-eth0/1)# manage ping
FW1(config-if-eth0/1)# manage telnet
FW1(config-if-eth0/1)# ip address 10.1.1.2 255.255.255.252
FW1(config-if-eth0/1)# exit
FW1(config)# interface ethernet0/2
FW1(config-if-eth0/2)# zone trust
FW1(config-if-eth0/2)# manage http
FW1(config-if-eth0/2)# manage ping
FW1(config-if-eth0/2)# manage telnet
FW1(config-if-eth0/2)# ip address 172.16.2.254 255.255.255.0
FW1(config-if-eth0/2)# exit
FW1(config)# ip vrouter trust-vr
FW1(config-vrouter)# ip route 0.0.0.0 0.0.0.0 10.1.1.1
FW1(config-vrouter)# exit
DCRS-5650模拟PCB
DCRS-5650-28(R4)(config)#hostname PCB
PCB(config)#vlan 233
PCB(config-vlan233)#int vlan 233
PCB(config-if-vlan233)#ip address 172.16.2.1 255.255.255.0
PCB(config-if-vlan233)#exit
PCB(config)#interface ethernet 1/0/1
PCB(config-if-ethernet1/0/1)#switchport access vlan 233
PCB(config-if-ethernet1/0/1)#exit
PCB(config)#ip route 0.0.0.0 0.0.0.0 172.16.2.254
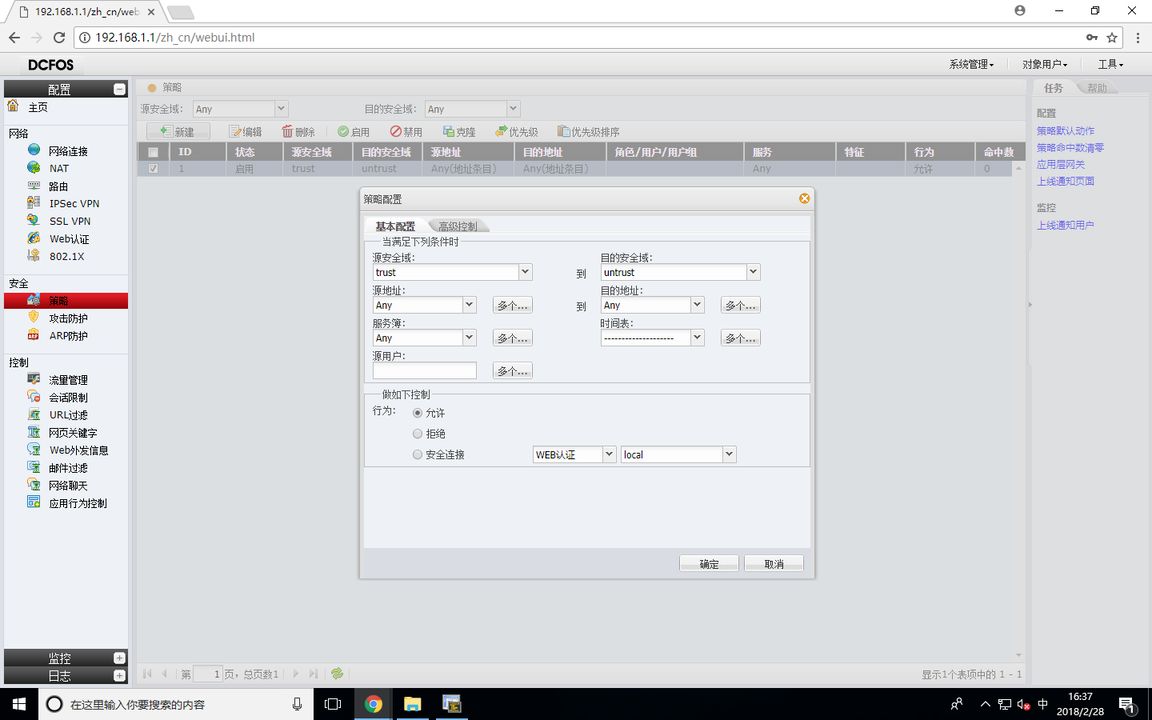
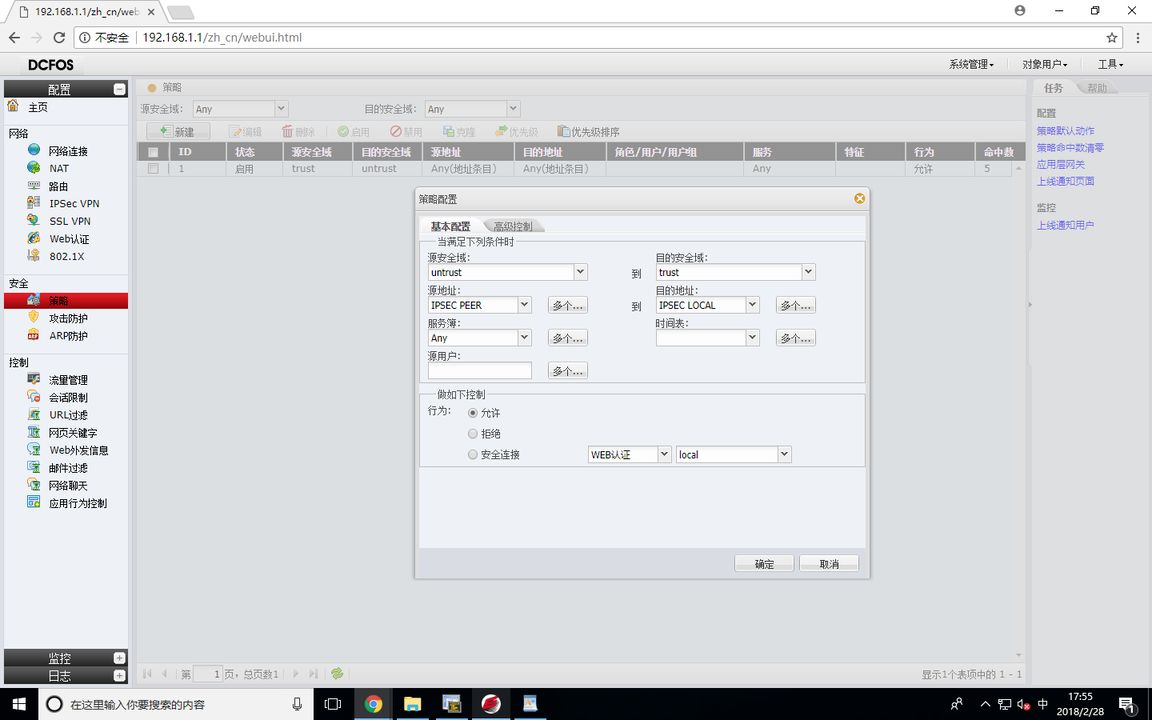
FW1配置策略
测试
PCB#ping 172.16.1.1
Type ^c to abort.
Sending 5 56-byte ICMP Echos to 172.16.1.1, timeout is 2 seconds.
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 0/6/33 ms
PCA#ping 172.16.2.1
Type ^c to abort.
Sending 5 56-byte ICMP Echos to 172.16.2.1, timeout is 2 seconds.
.....
Success rate is 0 percent (0/5), round-trip min/avg/max = 0/0/0 ms
此时PCB能ping通PCA,但PCA无法ping通PCB,因为现在防火墙只允许Trust到Untrust的数据流通过,防火墙默认设置拒绝所有数据流通过
配置IPSEC VPN
RT1
RT1_config#ip access-list extended 1
RT1_config_ext_nacl#permit ip 172.16.1.0 255.255.255.0 172.16.2.0 255.255.255.0 //匹配要进行IPSEC VPN的数据流
RT1_config_ext_nacl#exit
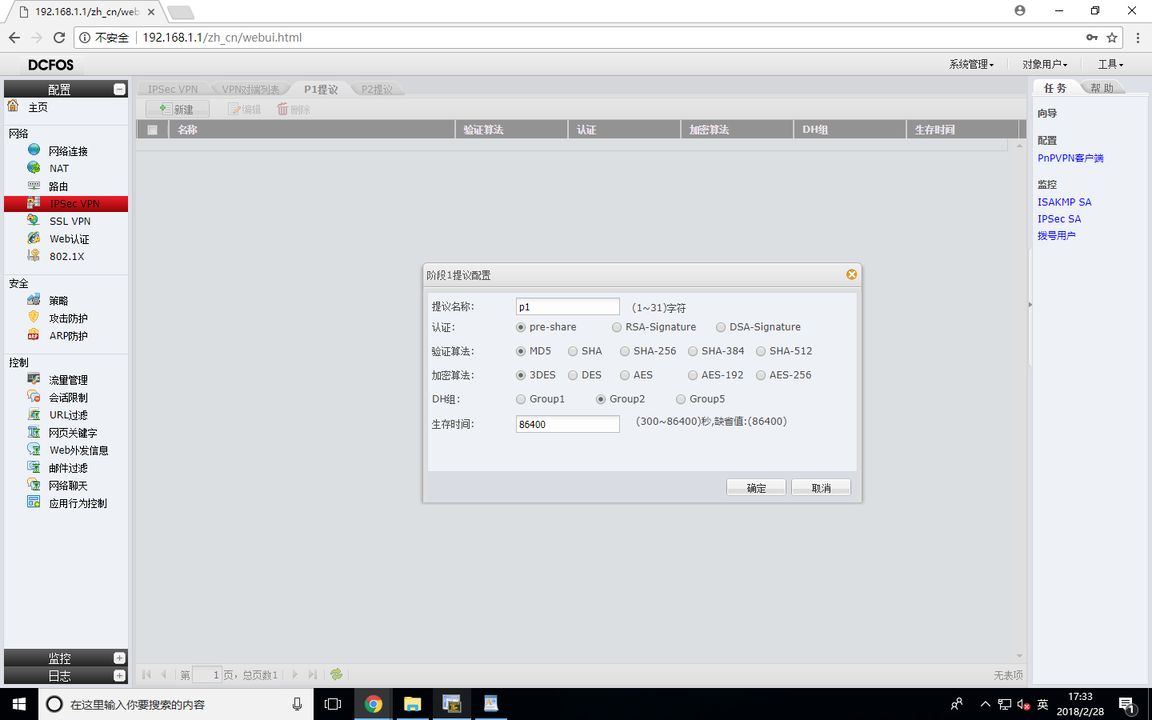
RT1_config#crypto isakmp policy 1 //设置IKE加密策略,里面的配置必须要与防火墙P1提议一致
RT1_config_isakmp#group 2 //DH组
RT1_config_isakmp#authentication pre-share //设置加密模式:共享密钥
RT1_config_isakmp#hash md5 //验证算法
RT1_config_isakmp#encryption 3des //加密算法
RT1_config_isakmp#exit
RT1_config#crypto isakmp key 123456789 10.1.1.2 //设置共享密钥
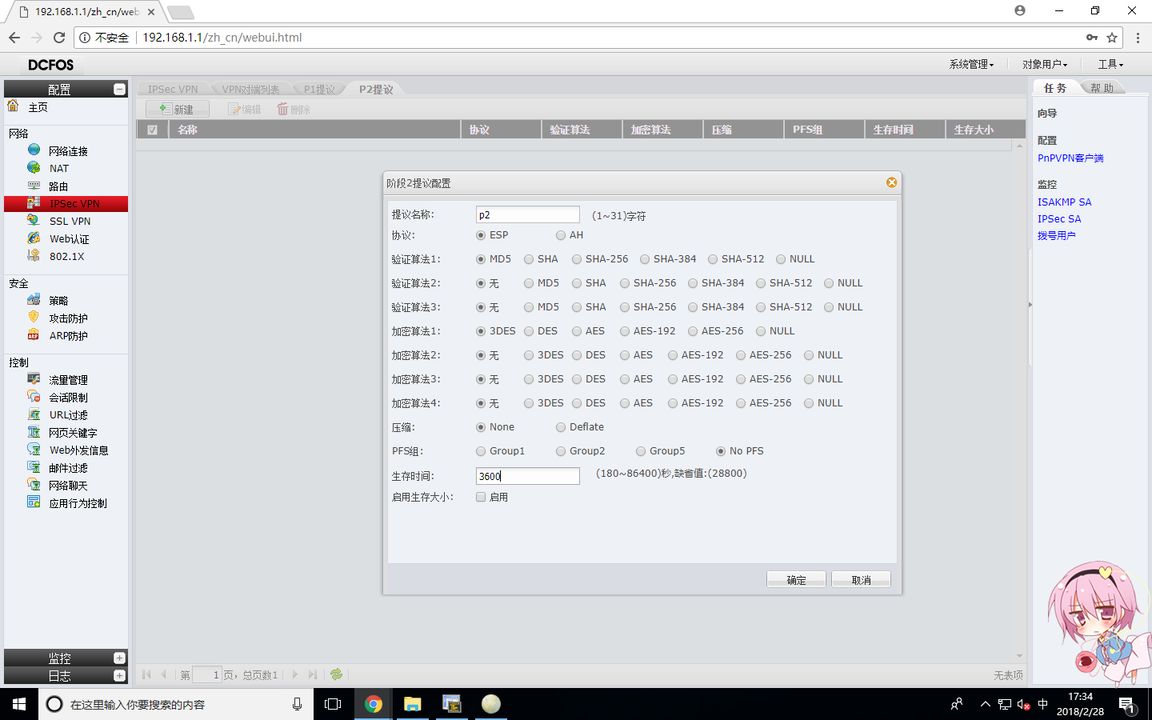
RT1_config#crypto ipsec transform-set 1 //设置隧道加密算法,里面的配置必须要与防火墙P2提议一致
RT1_config_crypto_trans#mode tunnel //设置为隧道模式
RT1_config_crypto_trans#transform-type esp-3des esp-md5-hmac //设置3des加密,md5验证
RT1_config_crypto_trans#exit
RT1_config#crypto map 1 10 ipsec-isakmp //设置加密映射表
RT1_config_crypto_map#match address 1 //绑定ACL
RT1_config_crypto_map#set peer 10.1.1.2 //设置VPN对端地址
RT1_config_crypto_map#set transform-set 1 //绑定交换集
RT1_config_crypto_map#exit
RT1_config#interface gigaEthernet 0/3
RT1_config_g0/3#crypto map 1 //应用加密映射表
RT1_config_g0/3#exit
FW1(P1提议)
FW1(P2提议)
FW1(VPN对端列表)
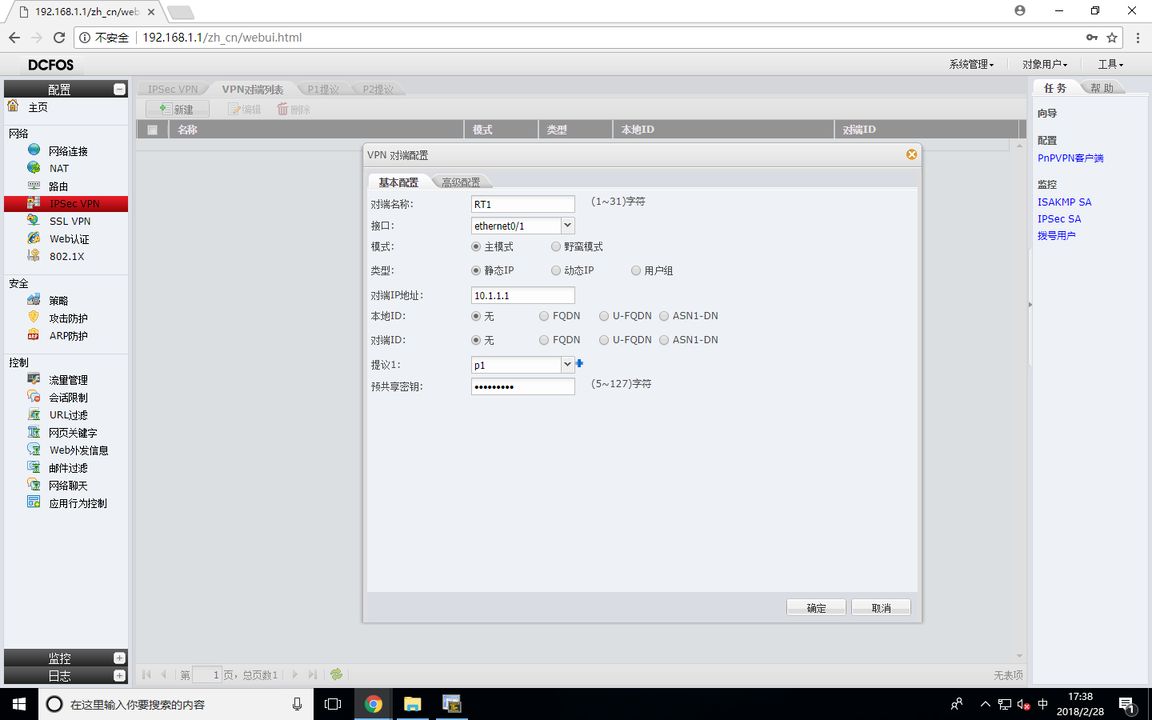
FW1(IKE VPN配置)
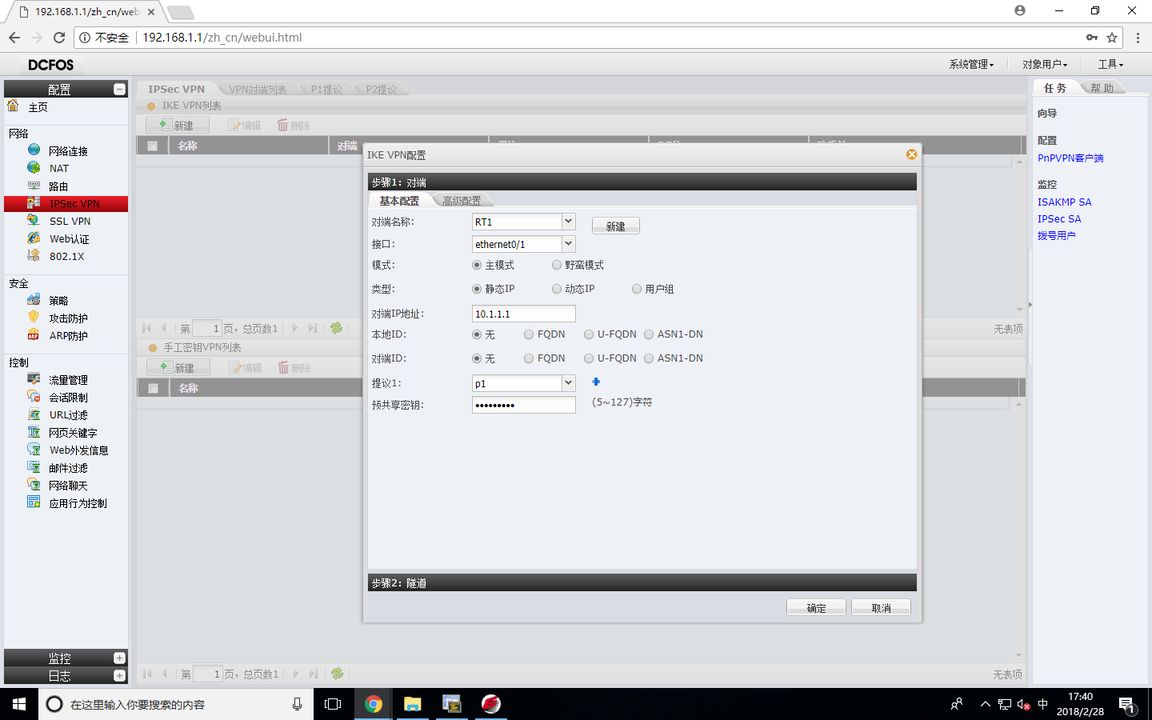
FW1(隧道加密配置)
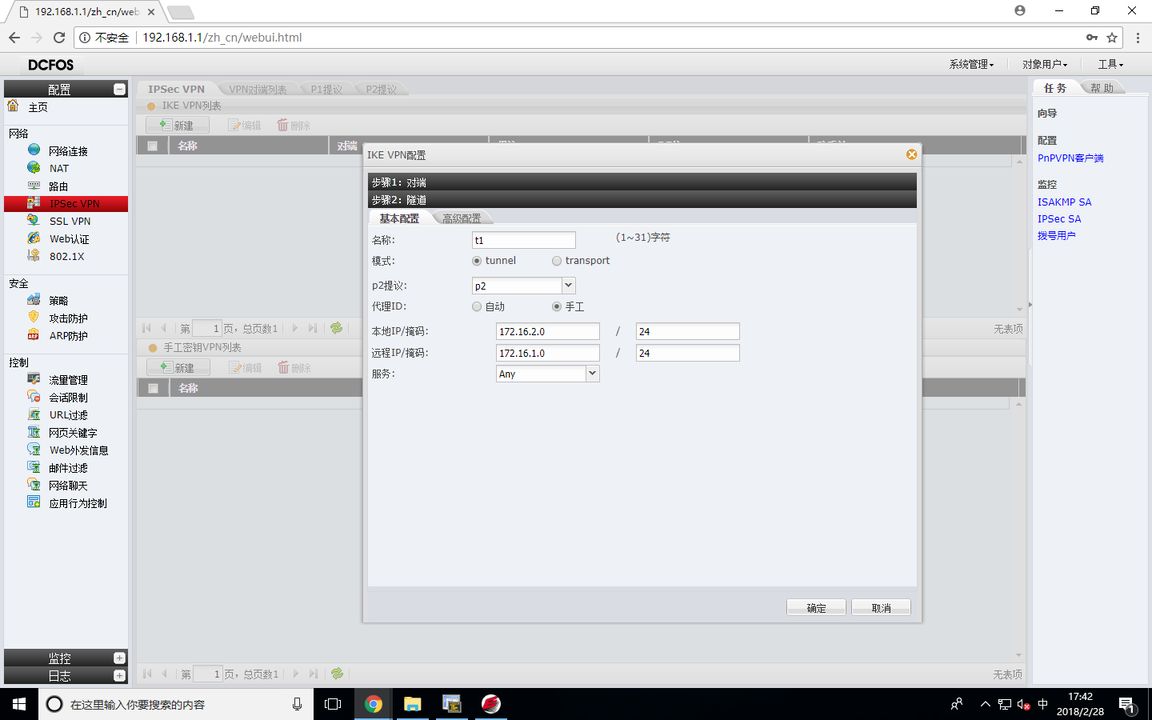
代理为需要加密的数据流,路由器里为ACL匹配加密数据流
FW1(隧道绑定配置)
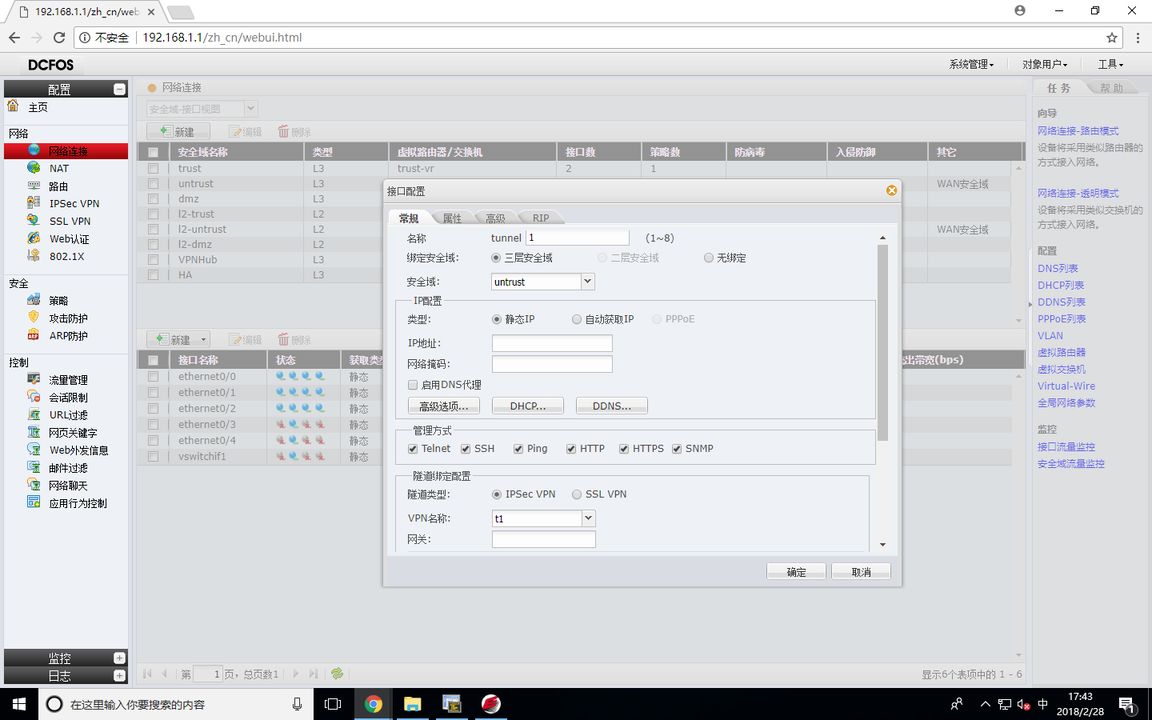
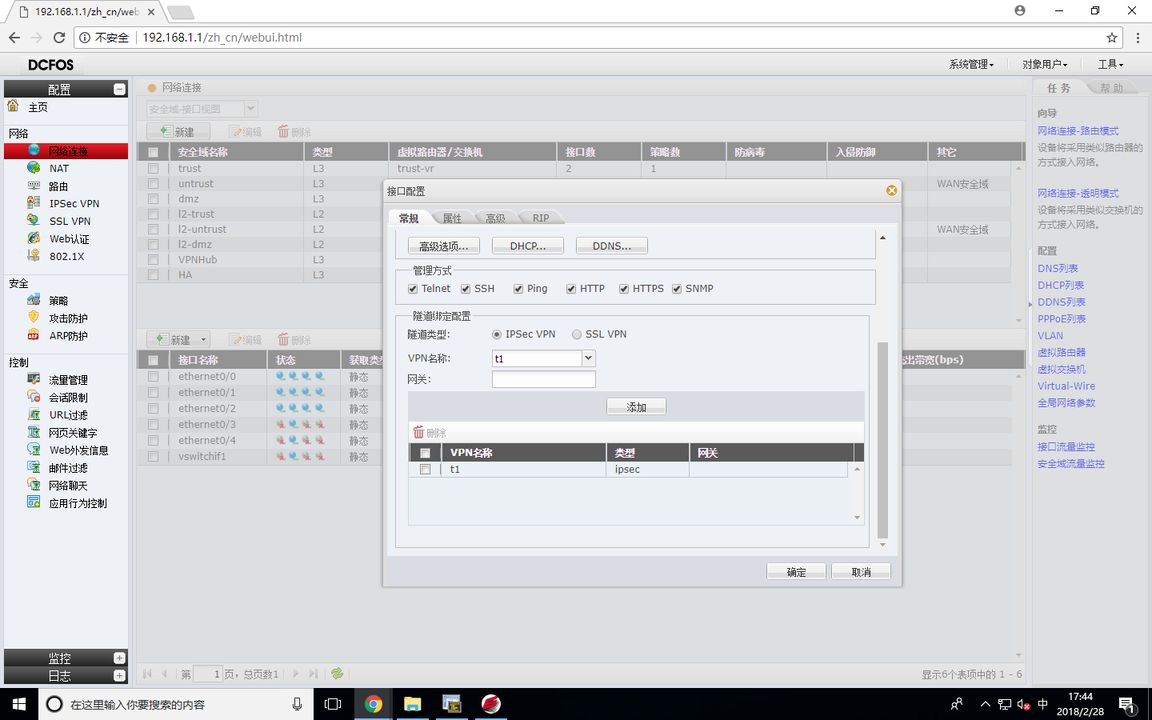
因为防火墙无法把加密映射表配置在E0/1上,只能用隧道接口进行绑定,所以要给个去往172.16.1.0/24的路由下一跳指向隧道接口,使其进行IPSEC VPN的加密
FW1(静态路由配置)
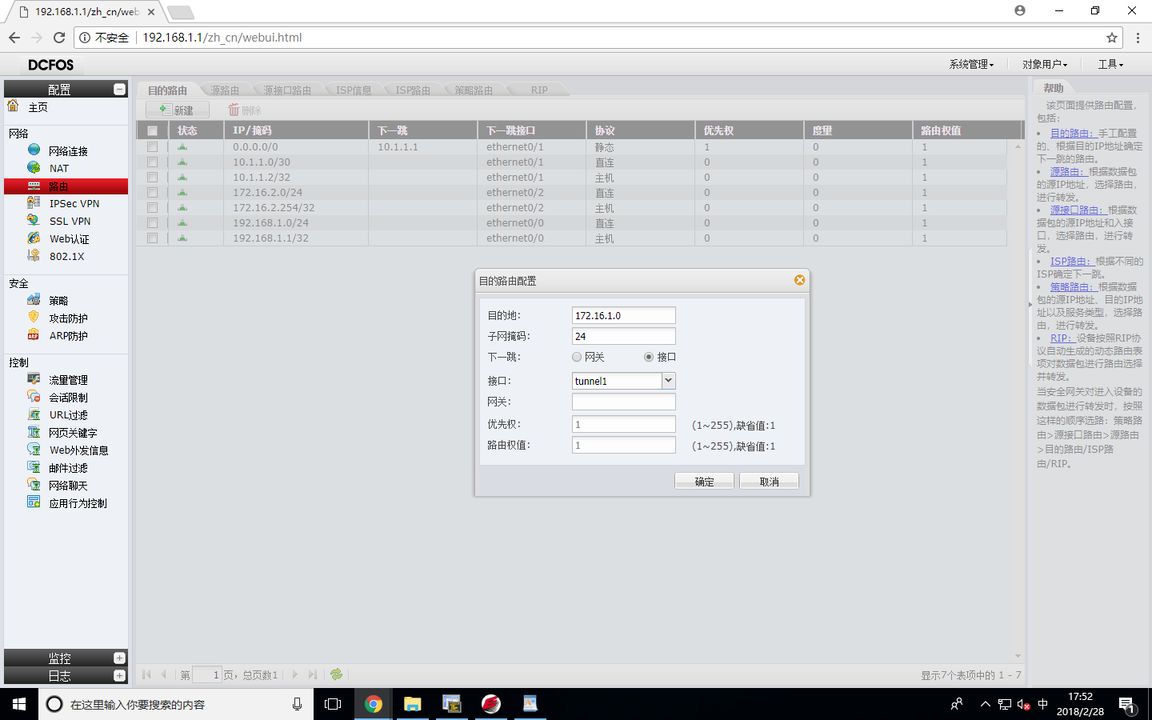
FW1(VPN地址池配置)
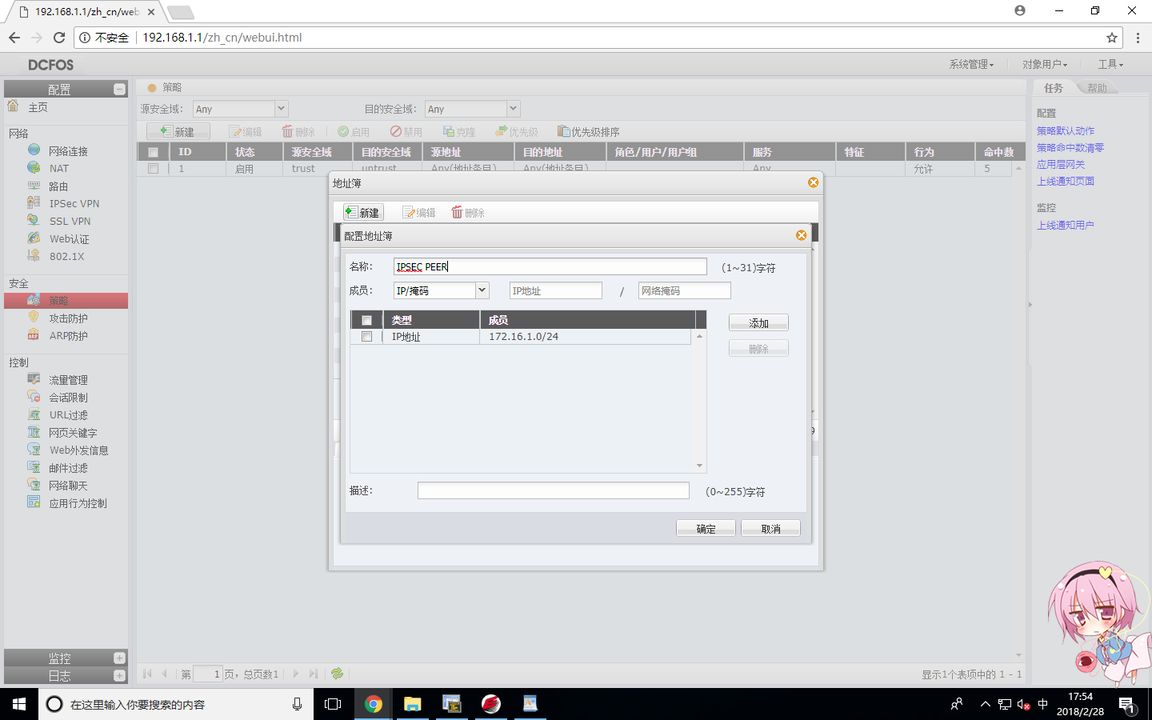
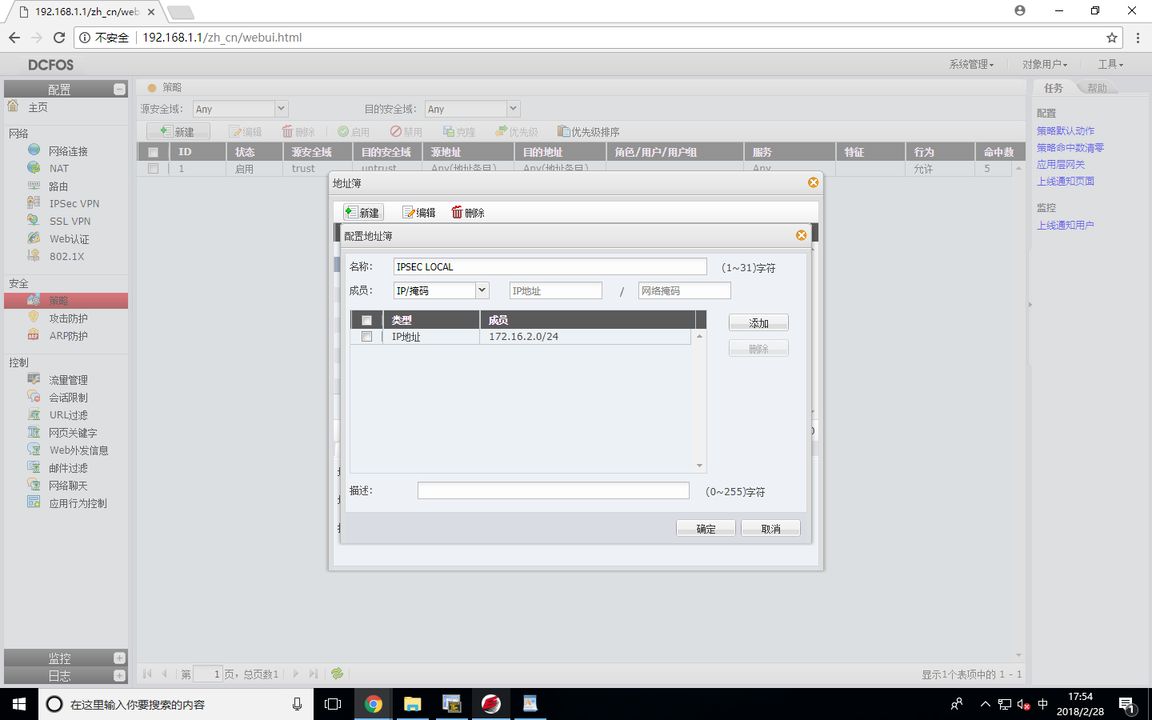
FW1(VPN策略配置)
测试
PCB#ping 172.16.1.1
Type ^c to abort.
Sending 5 56-byte ICMP Echos to 172.16.1.1, timeout is 2 seconds.
.!!!!
Success rate is 80 percent (4/5), round-trip min/avg/max = 0/0/0 ms
PCA#ping 172.16.2.1
Type ^c to abort.
Sending 5 56-byte ICMP Echos to 172.16.2.1, timeout is 2 seconds.
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 0/0/0 ms
查看IPSEC SA
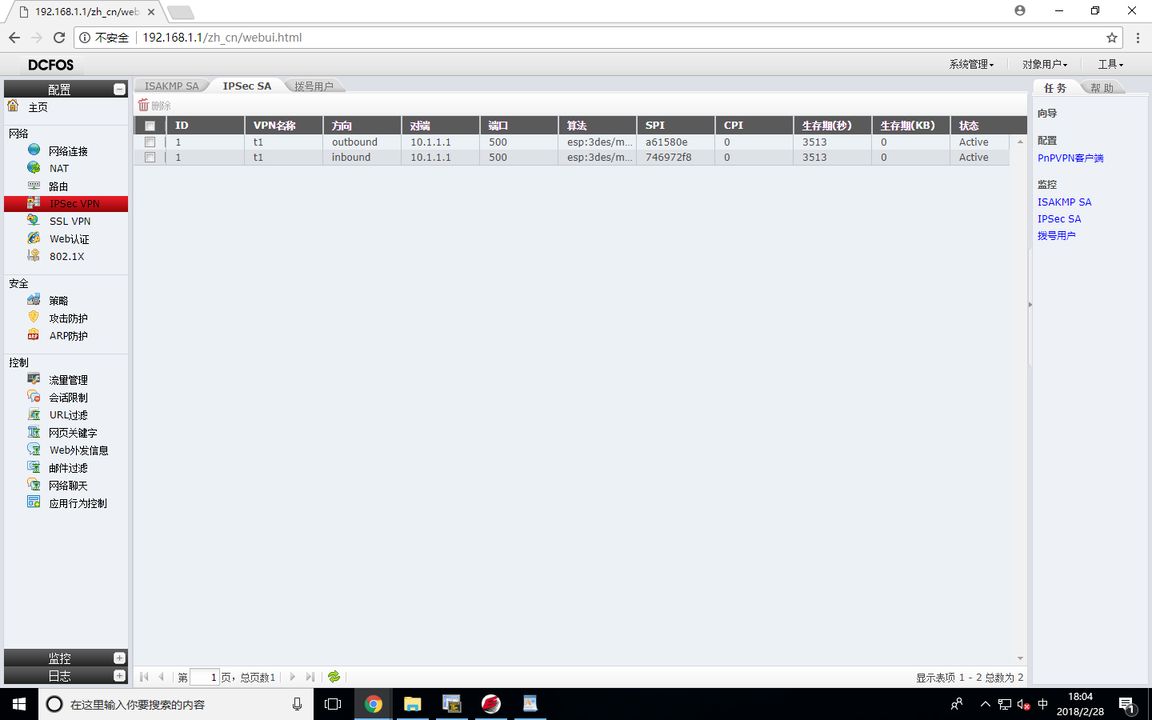
RT1#show crypto ipsec sa
Interface: GigaEthernet0/3
Crypto map name:1 , local addr. 10.1.1.1
local ident (addr/mask/prot/port): (172.16.1.0/255.255.255.0/0/0)
remote ident (addr/mask/prot/port): (172.16.2.0/255.255.255.0/0/0)
local crypto endpt.: 10.1.1.1, remote crypto endpt.: 10.1.1.2
inbound esp sas:
spi:0xa61580e(174151694)
transform: esp-3des esp-md5-hmac
in use settings ={ Tunnel }
sa timing: remaining key lifetime (k/sec): (4607999/3443)
outbound esp sas:
spi:0x746972f8(1953067768)
transform: esp-3des esp-md5-hmac
in use settings ={ Tunnel }
sa timing: remaining key lifetime (k/sec): (4607999/3443)
查看ISAKMP SA
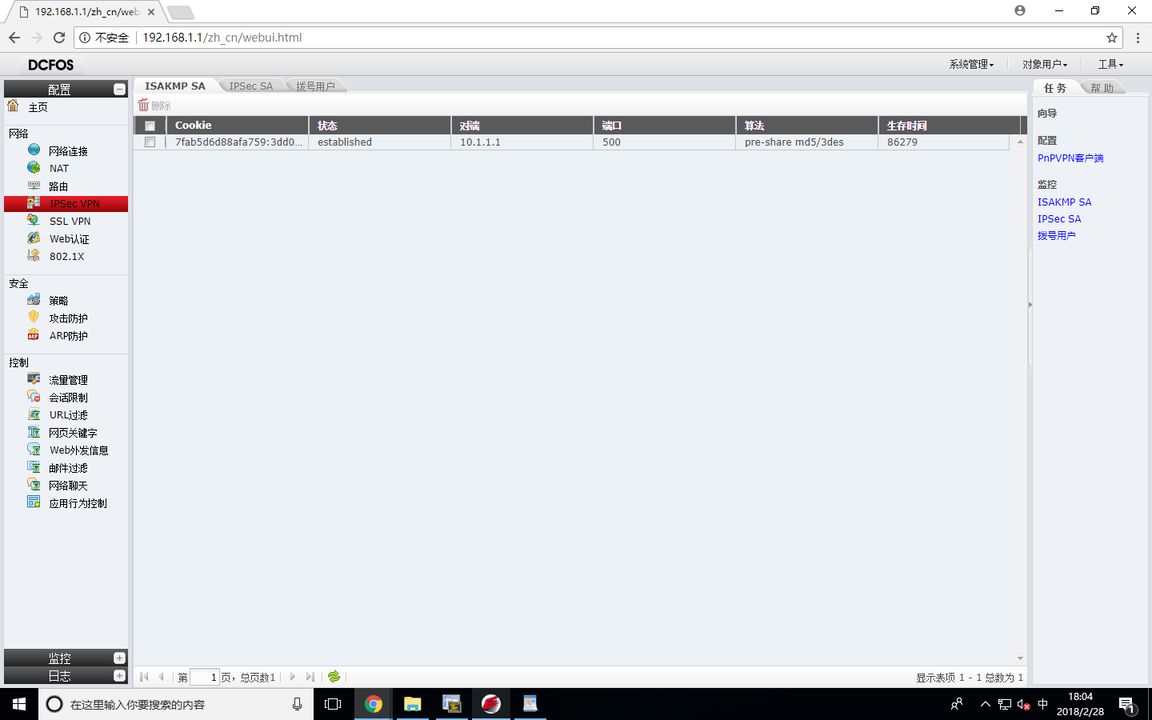
RT1#show crypto isakmp sa
dst src state state-id conn
10.1.1.2 10.1.1.1 <R>Q_SA_SETUP 3 6 1 10
10.1.1.2 10.1.1.1 <R>M_SA_SETUP 2 6 1 10

















1 条评论
SouFan · 2023年11月10日 下午9:20
可以,很详细